OSINT OPERATIONS and CROSS DOMAIN SOLUTIONS (CDS): How CDS can help OSINT activities and overcome technological challenges
OSINT or Open-source intelligence relates to the gathering of data through public sources which are processed, analyzed, and disseminated, so that this data becomes valued information/ intelligence. The data can be collected from various but only publicly available sources: commercial satellites images, internet, social media, etc.
OSINT showed its huge potential in the Ukrainian conflict, where open-source information is widely used both for intelligence gathering and for PSYOPS (Psychological Operations, such as disinformation campaigns). OSINT may also be seen as a real community where people share data and information, which is particularly seen in Ukraine because of the limited availability of traditional military systems and networks. Likewise, intelligence services, police and other public forces have increasingly recourse to it. Going even further, OSINT today is not only being used in military and security investigations, but also in several other areas like information/disinformation campaigns (e.g. elections) and even in commercial activities as support to business intelligence.
Looking at the conflict in Ukraine, OSINT may have made a real difference for Ukrainian troops to challenge Russia. Indeed, all data collected has been of great help, to better understand the situation, get accurate information and counter Russian disinformation campaigns. The use of satellite images made it possible to locate Russian troops, social media posts gave a clear picture of what was going on the ground. Cell phones and radio waves were used to spy on communications. One could say that it was the first time that a “conflict went online”.
With the Ukraine conflict, OSINT has – if not already happened – proven its usefulness for public actors in order to gain information superiority.
However, using OSINT and especially using the intelligence coming from it, may create a real technological – and regulatory- challenge for public actors. Indeed, once collected and analyzed, public actors must access this data/intelligence and transfer it to their own networks. But here comes the major challenge: such public actors (intelligence services, police, border agencies, etc.) manipulate classified or sensitive data and work on classified domains. The data collected from OSINT sources, which are inherently unclassified, may become sensitive and even classified when they are correlated and presented in specific intelligence products, such as reports.
Classified and sensitive information must be protected, and specific (cyber)security rules must be applied. One important rule is that a classified network may not be interconnected to a public network like Internet. This makes the collection and use of data complicated for public actors. They usually still work with air gapped systems, meaning that their classified network is physically isolated. Today, two main technology solutions are used for air gapping in OSINT applications.
The first, and more traditional solution, is the use of removable media such as USB sticks or similar. With the amount of data to be processed and the stringent velocity requirements imposed by the sometimes limited lifetime of this data (a post on a social network may bring information if analyzed in the first minutes after publication, after that its value decreases exponentially), traditional air gapping is not a viable solution anymore. Furthermore, the classified network may still be exposed to cyber risks from the use of removable media, which therefore needs to be sanitized, inspected and managed properly, with all the consequential overhead.
The second common solution used in OSINT for air gapping are the so called ‘web isolators’. These systems allow to transfer the representation of web content. Often they are based on creating a ‘virtual screenshot’ of the content which is then transferred to the HIGH security domain. This technology allows a certain degree of velocity in the data collection, but very soon reaches its limit, such as the lack of capability to transfer real contents like files and the lack of support to full bidirectional communication between security domains.
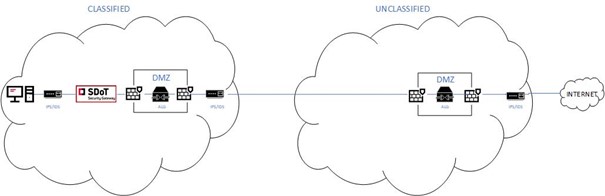
Cross Domain Solutions (CDS) can overcome this challenge. CDS is a technology developed to put an end to air gapped systems, as they enable the exchange of information between different security domains. CDS or Security Gateways control and if necessary, block the data flow between two security domains, at all layers. They operate based on data ruleset, Gateways inspect all data flow and checkthe data against security policies that are embedded into the Gateway. Therefore, only specifically approved data may leave the highest classified domain (HIGH). The filtering can also be implemented in the other direction, from the less trusted domain (LOW) to HIGH.
With CDS placed in the IT architecture, the data flow is totally secured: CDS prevents any not authorized data flowing out to the public network. With the creation of a DMZ, the combination with packet filter firewalls and IDS/IPS, the HIGH side is totally secured. So that no malicious data may sneak in.
The architecture looks as follows:
By allowing information exchange between a classified network and public sources, Security Gateways / Cross Domain Solutions present a real added value for the conduction of OSINT activities for public authorities. The technology:
- Protects classified domains and their data
- Supports digitization of OSINT activities by putting an end to air gap systems
- Prevents data leakage